Public-Private Keys and How they work in the blockchain realm

If you are new to crypto, you must be wondering about what are public and private keys. Bitcoin, as well as all other major cryptocurrencies, is built upon public-key cryptography, a cryptographic system that uses pairs of keys: public keys and private keys to authenticate transactions on the blockchain – send or receive funds.
When Bitcoins are sent to an address, what actually happens under the hood is that they are “locked up” in an unspent transaction output (UTXO), to only be “unlocked” (spent) in a later transaction if the condition -valid private key corresponding to a specific public key- in the UTXO are met.
What are private and public key?
Think of the public key similar to a bank account number. You share the account details with others to receive payments. Akin to a bank account’s secret PIN or password, private keys give the user access to the cryptocurrency on a given address. It unlocks the right to spend the associated cryptocurrencies and must remain known only to the user (or owner).
Each private key comes paired with a public key. The private key is a randomly generated string (numbers and letters) and the public key is mathematically derived from the private key. It’s a one-way function – Meaning It’s possible to recover the public key if you own the private key, however, it’s impossible to find the private key using the public key.
What are addresses then?
In the cryptocurrency transactions, the public key is represented by its digital fingerprint, called an address. The motivation for using hashes of public keys was to shorten the size of the address. It can be seen the same as the beneficiary named on a check (i.e. Pay to the order of).
Addresses are derived by applying a hash function (such as SHA3) on the public key. For example, in Ethereum, the resulting hash on the public key will be 64 characters long string. To get the final address take the last 40 characters and prefix with 0x.
Try out here: https://www.browserling.com/tools/sha3-hash
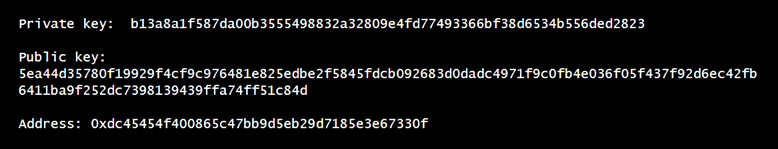
The motivation for using the public key hash was to shorten the size of the address. Note – hashing a public key has nothing to do with security. Whenever a transaction is spent from an address (hash public key), it reveals the public key as part of the script.
When using the wallets, the public keys are very rarely seen by the users. For the most part, public keys are stored inside the wallet file and managed by the wallet software. However, it is possible to send cryptocurrencies to either a public key or to the hash of a public key.
Use of these Public-Private keys in the blockchain
As explained above, the most common use of these key-pairs is to securely send or receive funds. Other than that, it allows access to decentralized applications. Like in real-world applications, we use Gmail to auto-login to Web2 applications, similarly, these key pairs help to interact with smart contracts of any decentralized application.
Other advance use of Public-Private keys in blockchain:
- For data encryption purposes. Using these keys users can share cryptographic messages with each other. Let’s say, Bob wants to send Alice an encrypted email. To do this, Bob encrypts his message with Alice’s public key. Then, when Alice receives the message, she takes the private key that only she has the knowledge to decrypt the message from Bob.
- Use as a digital signature to bind a person to the digital data. i.e. provide verification that the message was created by a known person and the message was intact and not altered in transit. In BFT consensus blockchain protocol, validators sign with their key to show authenticity or their agreements on the block produced.
What are mnemonics keys (or seeds)?
The public and private keys consist of a string of random numbers.
It looks something like this: HTyeXQeQcSwD5xLXV9tNKYmc8zMtdhAyhxm47sSS3uL2.
Not as easy as remembering your Gmail account ID and security password. Given the difficulty to remember crypto key-pairs, users need to store it somewhere safe. If a user loses the keys, especially private-key, they lose access to funds in the account. This can be a barrier to user adoption.
To make private keys user friendly, today most blockchains use Mnemonic keys. Mnemonic keys are a human-readable version of the private keys. Mnemonic is a way to reproduce something hard to remember. To a series of data like in private keys, random words are associated so as users can remember the original form.
Remember the phrase – ‘Some People Have Curly Brown Hair Turn Permanently Black’ from your school days. It’s a mnemonic form to remember Sin, Cos, and Tan trigonometric formulas.
Nowadays, most wallets use mnemonic seeds – 12,18 or 24-word easy to remember phrases that are tied to a given private key. The longer the phrase, the more complicated it becomes to figure out the correct combination.
This conversion goes through the method called BIP 39. BIP represents a proposed change to the bitcoin protocol. Using BIP 39 standards, 128-256 bits of random data is encoded to 12-24 word phrases. The selection of phrases is from the wordlist which contains 2048 words.
Users who own different blockchain protocol’s cryptocurrencies can easily manage funds with crypto wallets like Metamask or Trust wallet. This is done through the implementation of BIP 44 standard in the wallet. BIP 44 standard generates multiple blockchain addresses in the wallet’s account, and BIP39 generates one recovery mnemonic phrase that controls all the cryptocurrencies in their wallet account.


Comments are closed.