What Is Data Encryption
Data encryption is a process of translating data into another format that is not readable unless someone with the possession of a secret key (called a decryption key). Encryption is one of the common practices for effectively securing the data.
Encrypted data is a ciphertext that can be decrypted only with the correct key. Decrypted data is called plaintext, the intended information or message.
Understanding encryption keys:
Two main types of data encryption exist
- Symmetric encryption and
- Asymmetric encryption.
Symmetric encryption:
Symmetric encryption algorithms use the same key to perform both the encryption and decryption functions, while an asymmetric encryption algorithm uses a different key to encrypt and decrypt the data.
The key used for encryption in the symmetric method can be a word or string of characters or a number. After encryption, the data (plain text) is transformed into ciphertext and sent to the recipient. To decrypt the data the receiver needs the key which the sender used to encrypt it.
You can try symmetric encryption for yourself here: https://encipher.it/
An example encrypted message:
EnCt29c3486ee9e69fe3ddb0e9e3c90d9940e732e21cf9c3486ee9e69fe3ddb0e9e3cqe+xmS
EpjgHTsbtMCV1Q0AAm6UkSxXqvjDsjt5pAhGXNqw==IwEmS
The only way to make sense of this ciphertext is by decrypting the message which requires a key or a password.
The password to decrypt the above ciphertext is:
123
Looks simple. Right? however symmetric encryption has its own set of challenges. Let’s say Jim needs to send a confidential message to Sasha. He uses symmetric encryption to encrypt the message and sends this to Sasha.
Now, this adds a challenge for Jim i.e. how he can securely share the key with Sasha. What if during the process of sharing this key, some malicious actors intercept the key and can access this confidential information.
Symmetric cryptography has been used in the military, governments, and even by financial corporations. The challenges in managing secret-key gave rise to using asymmetric (or public key) cryptography.
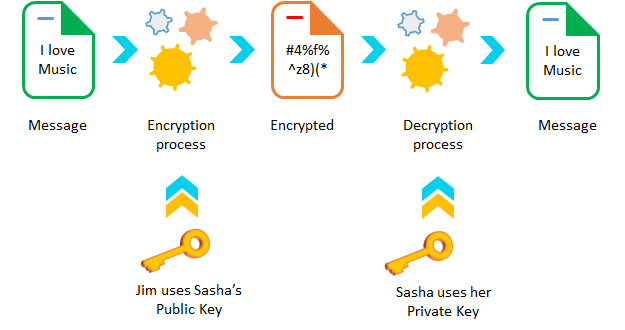
Asymmetric encryption solves this problem by using a key-pair.
Asymmetric encryption uses a key-pair to encrypt and decrypt the message. The public key for encryption and its associated private key for decryption.
Many of us have used the Public key and Private key to manage addresses on the blockchain.
The public key is openly available. Anyone can access the information on this address. In simple terms, knowledge of the public key only provides read-only access. In contrast, the private key authorizes the user to perform a transaction like a ‘write-access’.
Let’s take the above example, if Jim uses an asymmetric method, he will encrypt the message with Sasha’s public-key and sends her. Sasha can decrypt the message with her private key to its original form.
Even someone intercepts their messages, they will not be able to decrypt the message without knowing Sasha’s private key. This provides a high level of security.
Try out the asymmetric encryption algorithm here: https://8gwifi.org/rsafunctions.jsp
– Open the link in two separate windows. Lets call them Win1 and Win2.
– Copy the public key from Win2 and paste to the Win1.
– Type the text for Encrypt in Win1. The encrypted message can only be decrypted with the private-key from Win2.
– Now copy the encrypted text and paste in Win2 for decryption.


