51% Attack “Worst Fears A Reality For Ethereum Classic”
Ethereum Classic got hacked using a 51% attack. More than $1 million worth of ETC stolen so far. The hack was first noticed by Coinbase and alerted the community about detecting “a deep chain reorganization of the Ethereum Classic blockchain“.
According to most analysts, the hack could be as a result of the new 1.4 GH/s ETHash ASICs. This has caused a public outcry to ban these chips both on the Ethereum Classic and Ethereum networks.
The analysis reveals the attack started on Jan. 5th and lasted until Jan. 87, making it one of the longest 51% attack ever recorded.
As per our analysis, the attacker had a hash rate equivalent to 6254 GH/s [Gigahash per second], which is about more than 60% of the total hash rate available for the entire Ethereum Classic network.
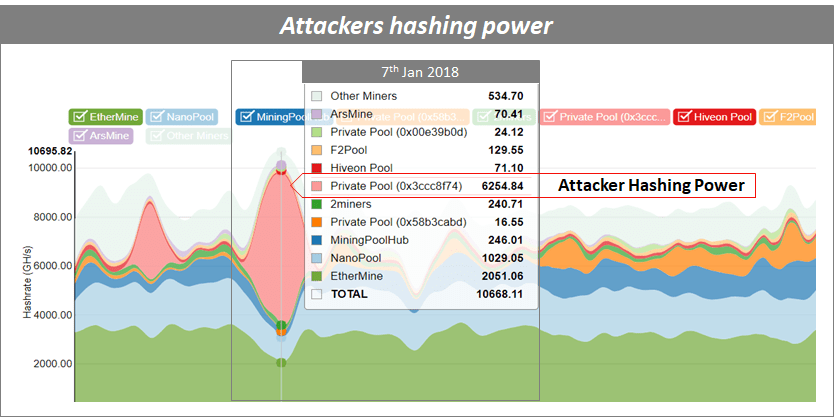
Ethereum Classic attack could be a wake-up call for cryptocurrencies using ‘Proof-Of-Work’.
According to Nir Kabessa, President of Blockchain at Columbia University,
“The distributed ledger community at large should consider a deep re-evaluation of ‘Proof-Of-Work’ security profile. However, coordinating attacks on those larger, cornerstone networks would be orders of magnitude more difficult.”
As a result of this, many exchanges and platforms halted ETC-related services.
Latest Update:
On 10th Jan, Gate.io, one of the affected exchanges found that the attacker returned partial ETC back to Gate.io (100k USD). The company tried contacting the attacker but didn’t get any reply.
If the attacker didn’t run it for profit, he might be a white hacker who wanted to remind people of the risks in blockchain consensus and hashing power security.
According to the statement from Gate.io published on 12th Jan,
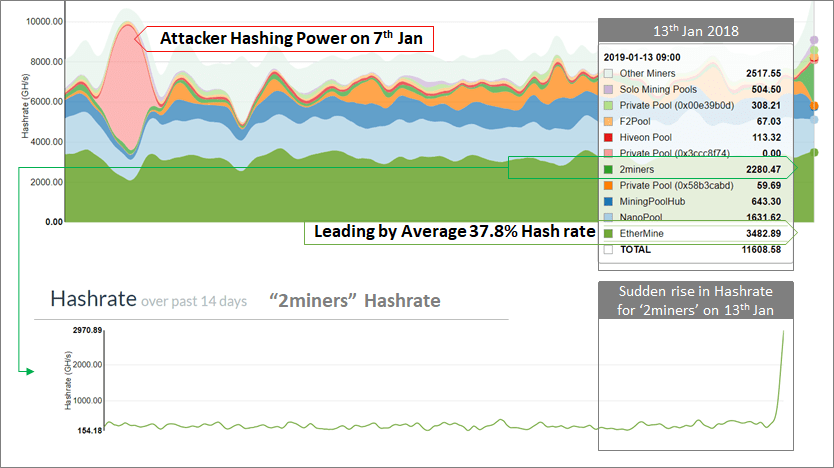
As per our analysis, the hashing power of the Ethereum Classic network is still not strong enough and it’s still possible for any cynical miner to launch another 51% attack.
What is 51% Attach and Reorganization
If a single miner or group of miners can assemble more than 50% hashing power then, this will allow the attacker to create a separate chain from any previous block in the blockchain. Given that it has the majority of computing power, its new chain will eventually overtake the accepted chain by the network, thereby defining a new transaction history.


Comments are closed.