How Digital Signature Work And Use In Blockchain
The likelihood of a dispute over the exchanged message in crucial business applications is very high. Therefore, the receiver needs assurance that the message came intact from the intended sender and s/he should not be able to repudiate the origination of that message.
It is common practice in real-world to use handwritten signatures on a paper to bind an agreement since pen-and-paper signatures are hard to tamper. For example, say Bob buys a Car for $10,000 and writes a cheque as payment. The signature guarantees that only Bob could have signed the cheque. Therefore, Bob’s bank must pay the cheque.
Similarly, a digital signature is a cryptographic technique that binds a person to the digital data. i.e. provide verification that message was created by a known person and the message was intact and not altered in transit.
In financial transactions, software license distribution, etc digital signatures are used to implement electronic signatures. NOTE: Not all electronic signatures use digital signatures.
Electronic signatures have legal significance in countries like the United States Of America, Algeria, Turkey, India, Brazil, Indonesia, Mexico, Saudi Arabia, Uruguay, Switzerland and the countries of the European Union.
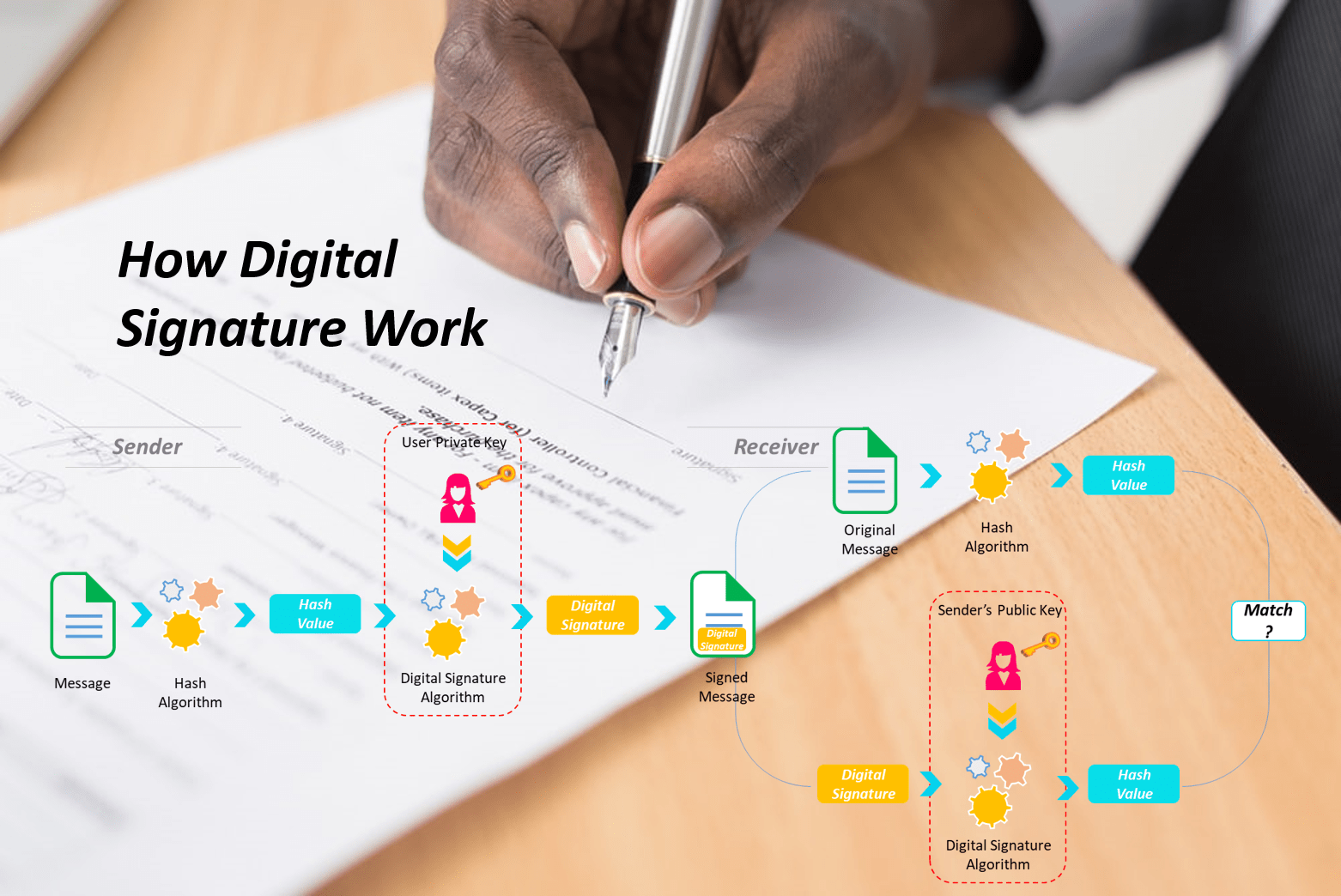
The following process illustrates how a digital signature works:
Generate the hash of the data
Signer feeds the data to the hash function and generates the hash of data. The value of this hash is unique to the data.
Produce digital signature
Hash value and private key are then fed to the signature algorithm which produces the digital signature on a given hash.
Send to recipient
The user then sends the data with the digital signature to the intended receiver.
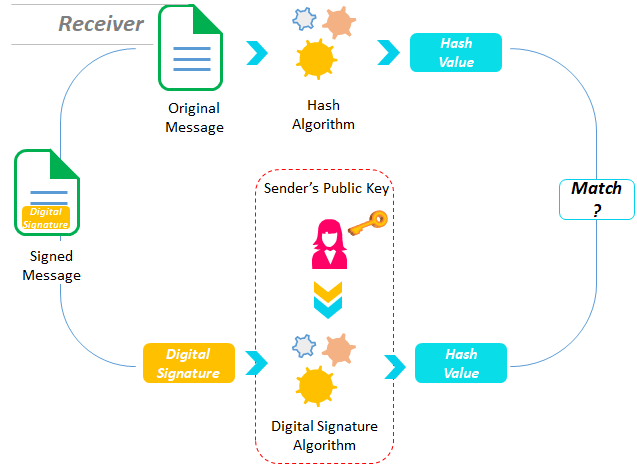
The receiver checks the hash value generated by the sender
After receiving the data and signature on it, the receiver feeds the sender’s public key and the digital signature into the algorithm. It generates a hash value as output.
Regenerate hash value from the data and match with hash sent by the sender
Additionally, the receiver uses the same hash function and generates the hash value of the original data. If this freshly generated hash value matches the hash value from the previous step 4, the receiver gets the assurance that the digital signature is valid.
You can try experimenting with digital signature here: https://www.signinghub.com
Advantages of Digital Signatures
Digital signatures are the most secure cryptography method for achieving information security. The receiver confirms message authentication by validating the digital signature with the public key of the sender. Also can be sure that s/he is communicating with whom they intend to.
Also, in case an attacker has access to the data and modifies it, the hash of modified data and the output provided by the verification algorithm will not match. Hence, the receiver can safely deny the message assuming that data integrity has been breached.
Apart from providing message authentication and data integrity, digital signatures also provide non-repudiation of message. Since it is assumed that only the signer (sender) has the knowledge of the signature key, thus the receiver can present the data and digital signature to a third party as evidence if any dispute arises in the future.
How it relates to Blockchain:
- Consensus algorithm. In pBFT consensus, the leader uses the digital signature to collect votes from the nodes to confirm the new block.
- Digital signatures as a legal binding. Signers use their private key to sign the digital legal contract. Thus the parties involved can present digital signature as evidence.
- Multisignature used in exchange wallets. A digital signature scheme with the requirement of more than one signee to approve a transaction. A joint signature means that no single person could access the wallet without the awareness of at least one other person.

